The Ignore List is a powerful feature that allows you to exclude trusted files and websites from future scans and security checks. Sometimes legitimate files or safe websites may be flagged as potential threats by security software. By adding these items to your Ignore List, you can prevent false positives and streamline your security experience.
Understanding the Ignore List
The Ignore List prevents Gridinsoft Anti-Malware from detecting specific files and blocking certain websites that you know to be safe. This feature is essential for users who work with specialized software or visit websites that may trigger security alerts due to their nature or content, even when they pose no actual threat.
You can add items to the Ignore List in two ways:
- During Detection: Add files or URLs immediately when they’re flagged during a scan
- Manual Addition: Proactively add files or websites through the Ignore List interface
Accessing the Ignore List
Gridinsoft Anti-Malware provides two convenient ways to access the Ignore List:
Method 1: Through the Scan Tab
In the Scan tab, look for the text “N items in Ignore List” in the lower-right corner of the interface. Click this link to access the Ignore List directly.

Method 2: Through the Tools Tab
Navigate to the Tools tab and locate the Exclusions section in the bottom-right area. Click the Ignore List button to open the management interface. When you navigate back from the Ignore List, you’ll return to the Tools tab.

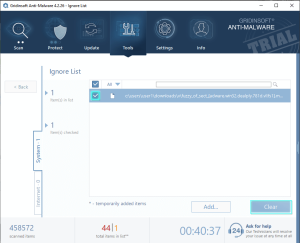
Ignore List Interface
The Ignore List interface contains two main tabs for different types of exclusions:

System Tab
Use this tab to manage file exclusions. Files added here will be ignored during system scans, preventing them from being flagged as potential threats.
Internet Tab
This tab manages website and URL exclusions for Gridinsoft’s Internet Protection service. URLs added here will not be blocked by the web filtering system.
Adding Items to the Ignore List
Both tabs contain Add and Clear buttons for managing your exclusions:
Adding Files (System Tab)
To add a file to the Ignore List:
- Click the Add button in the System tab
- Use the file explorer window to navigate to and select the file you want to exclude
- Confirm your selection
Adding URLs (Internet Tab)
To add a website or URL to the Ignore List:
- Click the Add button in the Internet tab
- Enter the URL you want to exclude
- Choose your exclusion options

URL Exclusion Options
When adding a URL, you have several configuration options:
- Single URL: Exclude only the specific page or link
- Entire Domain: Exclude all pages within the domain (recommended for trusted websites)
- Session-Only: Apply the exclusion only for the current session (temporary exclusion)
Choosing the Right Option:
Select “Entire Domain” when you trust a website completely and want to access all its pages without restrictions. Choose “Single URL” for specific pages that may contain content that triggers false positives.
Removing Items from the Ignore List
To remove files or URLs from the Ignore List:
- Navigate to the appropriate tab (System for files, Internet for URLs)
- Locate and select the item you want to remove
- Click the Clear button
- Confirm the removal
Adding Items During Scan Detection
You can add detected items to the Ignore List directly from scan results, which is often the most convenient method:
Enabling Advanced Options
After a scan completes and displays detected threats, ensure that Advanced Options are enabled using the switch above the results list. This reveals action bars that show what action will be applied to each detected item.

Adding Individual Items
To add a specific detected item to the Ignore List:
- Locate the small arrow to the right of the threat entry
- Click the arrow to open the dropdown menu
- Select “Ignore always” from the options
Adding All Items
To add all detected items to the Ignore List:
- Click the arrow next to “Apply to all” in the list header
- Select “Ignore always” from the dropdown menu
- Confirm your decision
Important Security Considerations:
- Only add files and websites to the Ignore List if you are completely certain they are safe
- Regularly review your Ignore List to ensure it only contains items you still trust
- Be cautious when using “Apply to all” – ensure all detected items are genuinely safe
- When in doubt, contact our support team for guidance on whether an item should be ignored
Best Practices for Ignore List Management
To maintain optimal security while using the Ignore List effectively:
- Regular Reviews: Periodically review your Ignore List to remove outdated or unnecessary exclusions
- Specific Exclusions: Use specific URLs rather than entire domains unless you completely trust the website
- Documentation: Keep notes about why certain items were added, especially for business environments
- Conservative Approach: When uncertain about an item’s safety, err on the side of caution and don’t add it to the list
The Ignore List is a powerful tool for customizing your security experience, but it should be used thoughtfully to maintain the highest level of protection for your system.
